- The CyberLens Newsletter
- Posts
- AI Driven Incident Response as the New Operational Backbone of Cyber Defense
AI Driven Incident Response as the New Operational Backbone of Cyber Defense
A disciplined convergence of intelligence automation resilience and human judgment

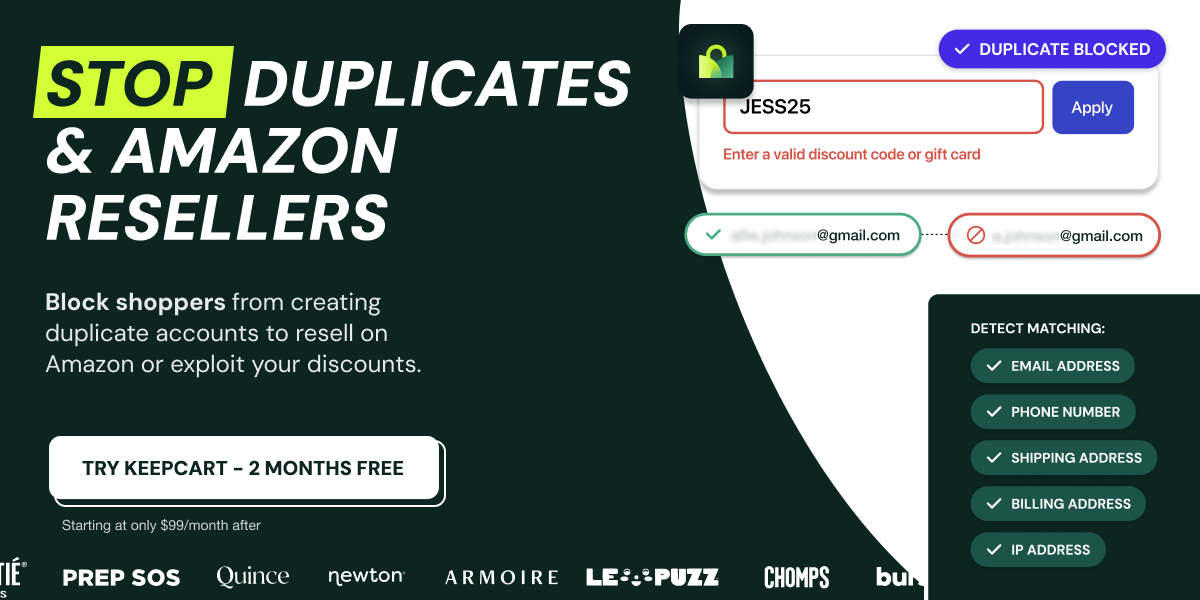
Stop Duplicates & Amazon Resellers Before They Strike
Protect your brand from repeat offenders. KeepCart detects and blocks shoppers who create duplicate accounts to exploit discounts or resell on Amazon — catching them by email, IP, and address matching before they hurt your bottom line.
Join DTC brands like Blueland and Prep SOS who’ve reclaimed their margin with KeepCart.

🧠💾 Interesting Tech Fact:
One little-known precursor to modern incident response emerged in the 1960s within mainframe time-sharing systems, where operators used handwritten “fault logs” to correlate system crashes with user activity patterns over weeks or months. These logs were manually analyzed to predict future failures and isolate malicious misuse long before intrusion detection systems existed. In effect, early administrators practiced a primitive form of behavioral analysis and post-incident learning, laying conceptual groundwork for today’s AI-driven response models—without algorithms, dashboards, or automation, only disciplined observation and operational intuition 📜⚙️.
Introduction: AI Driven Incident Response as a Foundational Security Discipline
Artificial intelligence–driven incident response represents a structural shift in how modern organizations confront cyber threats. Rather than treating security incidents as isolated technical failures, AI-enabled response frameworks interpret them as evolving signals within complex digital ecosystems. These systems continuously observe, correlate, and contextualize telemetry across cloud platforms, endpoints, identities, applications, and data flows, allowing defenders to recognize malicious activity at machine speed without forfeiting strategic oversight.
At its core, AI cybersecurity incident response is the orchestration of detection, analysis, containment, eradication, and recovery through intelligent automation informed by probabilistic reasoning and learned behavior. It does not replace human expertise; instead, it extends cognitive reach. Security teams gain the ability to reason across volumes of data that exceed human scale, transforming response operations from reactive firefighting into disciplined operational control.

The Organizational Imperative for Intelligent Response
Organizations adopt AI-driven incident response because the velocity and asymmetry of modern attacks render manual processes insufficient. Adversaries leverage automation, generative tooling, and adaptive infrastructure to compress attack timelines, often achieving impact before traditional response mechanisms engage. AI-based response counters this compression by accelerating triage, prioritization, and action without relying on static rule sets alone.
Equally important is governance alignment. Executive leadership increasingly demands demonstrable cyber resilience, not just compliance. AI incident response platforms provide measurable outcomes such as reduced mean time to detect, reduced mean time to contain, and defensible decision trails. These metrics bridge technical execution with enterprise risk management, enabling security leaders to justify investments and communicate operational posture in language the board understands.
Timing and Context in AI Cybersecurity Response Activation
AI-driven incident response is utilized continuously rather than episodically. Unlike legacy approaches that activate only after an alert crosses a predefined threshold, intelligent systems operate persistently, evaluating weak signals, behavioral drift, and contextual anomalies long before an incident is formally declared. This continuous posture allows organizations to intervene earlier in the attack lifecycle, often preventing escalation altogether.
The moment of formal activation still matters. When AI systems elevate confidence levels beyond acceptable risk tolerance, structured response workflows engage automatically or semi-automatically. These workflows account for business context, asset criticality, regulatory exposure, and operational dependencies. The result is a response that is not merely fast, but proportionate, legally aware, and operationally sustainable.
Methods and Mechanisms of AI Enabled Incident Response
AI cybersecurity incident response relies on a combination of analytical methods that collectively enhance situational awareness. Machine learning models identify deviations from baseline behavior, while graph analysis maps relationships between users, systems, and processes. Natural language processing assists analysts by summarizing incidents, correlating threat intelligence, and generating human-readable narratives from raw data.
These methods enable structured response actions such as automated containment, adaptive access revocation, and prioritized forensic preservation. Importantly, response decisions are not binary. Confidence scoring and probabilistic reasoning allow systems to recommend graduated actions, preserving business continuity while reducing attacker dwell time.
Core AI incident response capabilities typically include:
Behavioral anomaly detection across users workloads and data
Automated enrichment using internal and external intelligence
Risk-based incident prioritization and scoring
Machine-assisted root cause analysis
Adaptive containment and isolation mechanisms
Evidence preservation with chain-of-custody awareness
Analyst decision support through contextual summarization

Architectural Models Supporting AI Incident Response
Architectural models for AI-driven incident response determine whether intelligence enhances resilience or merely accelerates disorder. At enterprise scale, incident response architecture is not a single platform or product, but a layered operational system designed to ingest vast telemetry, contextualize uncertainty, and coordinate proportionate action across heterogeneous environments. The strength of these architectures lies in how well they balance speed, interpretability, and governance under adversarial pressure.
At a structural level, effective AI incident response architectures are designed around continuous sensing, contextual intelligence, and orchestrated enforcement. These layers must function independently yet remain tightly integrated, allowing organizations to respond dynamically without introducing single points of failure or opaque decision-making. The architecture itself becomes a control mechanism—one that enforces discipline even as threats evolve.
Telemetry-Centric Foundations and Data Gravity
The foundation of any AI incident response architecture is a telemetry-first design. Security-relevant data is no longer limited to logs or alerts; it encompasses identity behavior, API calls, workload execution paths, network flows, and data access patterns. Modern architectures recognize that response quality is bounded by observational depth. As such, they emphasize normalized, time-synchronized telemetry pipelines capable of supporting real-time and retrospective analysis.
These pipelines are deliberately decoupled from response logic. Data gravity—the tendency for data to accumulate where it is generated—is respected through edge collection and local preprocessing, while centralized analytics layers perform correlation and learning. This hybrid approach minimizes latency while preserving global visibility, ensuring AI models reason across environments without overwhelming infrastructure or analysts.
Intelligence Layers and Contextual Reasoning
Above telemetry ingestion sits the intelligence layer, where AI models transform raw signals into operational insight. This layer is not monolithic. It is composed of complementary analytical mechanisms, including behavioral baselining, anomaly detection, graph-based relationship analysis, and probabilistic risk scoring. Each mechanism contributes partial understanding; together, they form a multidimensional view of the incident landscape.
Crucially, mature architectures treat intelligence as contextual rather than absolute. AI systems incorporate asset criticality, user roles, business processes, and regulatory exposure into their reasoning. Anomalous behavior is not evaluated in isolation but weighed against environmental norms and operational risk. This contextualization prevents overreaction while ensuring high-confidence threats receive decisive attention.
Decision Mediation and Human-in-the-Loop Control
One of the most defining characteristics of robust AI incident response architectures is the presence of a decision mediation layer. Rather than allowing AI outputs to directly trigger enforcement actions, this layer evaluates confidence thresholds, policy constraints, and escalation criteria. It serves as the boundary between inference and action.
Human-in-the-loop control is preserved not as a concession to mistrust, but as a structural safeguard. Analysts are presented with ranked options, explanatory signals, and projected outcomes, enabling informed intervention when ambiguity remains. This design ensures accountability, supports analyst trust, and maintains organizational alignment with legal and ethical obligations.
Response Orchestration and Adaptive Enforcement
Response orchestration layers translate decisions into coordinated actions across security and operational controls. These actions may include access revocation, workload isolation, network segmentation, credential invalidation, or forensic snapshotting. Architecturally, orchestration engines are modular, API-driven, and policy-aware, allowing responses to be scaled or constrained based on incident severity.
Adaptive enforcement distinguishes advanced architectures from rigid automation. Actions are reversible, staged, and context-sensitive. For example, an identity may be temporarily constrained rather than fully disabled, or a workload may be quarantined in observation mode before termination. This graduated approach preserves business continuity while still reducing attacker dwell time.
Explainability, Auditability, and Governance Alignment
In regulated and high-assurance environments, explainability is not optional. AI incident response architectures must expose reasoning paths, confidence scores, and decision criteria in forms that can be reviewed by security leadership, auditors, and legal teams. Explainability is achieved through model transparency, structured metadata, and narrative generation layers that translate machine reasoning into human-readable records.
Auditability is architected from the outset. Every decision, recommendation, and enforcement action is logged with temporal precision and contextual reference. This creates defensible incident records that support post-incident review, regulatory reporting, and organizational learning. Governance alignment is reinforced by embedding policy controls directly into response workflows rather than applying them retrospectively.
Resilience Through Distributed and Fault-Tolerant Design
AI incident response architectures are themselves targets. As such, resilience is built through distribution, redundancy, and graceful degradation. Critical components—telemetry ingestion, analytics, orchestration—are isolated to prevent cascading failure. If intelligence layers are impaired, baseline detection and manual workflows remain functional, ensuring continuity of response.
Fault tolerance extends to decision logic. Architectures assume imperfect data, partial visibility, and adversarial manipulation. By weighting signals probabilistically and avoiding hard dependencies on single data sources, systems maintain operational integrity even under degraded conditions.
Learning Feedback Loops and Architectural Evolution
The most consequential feature of AI incident response architecture is its capacity for learning. Feedback loops capture analyst decisions, incident outcomes, and false-positive resolutions, feeding them back into model refinement and policy tuning. Architecture becomes evolutionary rather than static, adapting to organizational change and adversary innovation alike.
Over time, this learning reshapes response posture. Recurring attack patterns are recognized earlier, control gaps are surfaced structurally, and response strategies mature from containment toward anticipation. The architecture thus functions not merely as a response engine, but as a mechanism for sustained defensive intelligence.
In sum, architectural models supporting AI incident response define how intelligence is operationalized under pressure. When thoughtfully designed, they impose order on uncertainty, preserve human judgment, and enable organizations to respond with precision rather than panic. These architectures do not promise perfect security; they promise something more durable—clarity, adaptability, and control when failure is no longer hypothetical but imminent.

Integrating AI Response into Enterprise Security Frameworks
Integration begins with aligning AI incident response capabilities to existing security frameworks and operating models. Rather than introducing parallel processes, organizations should map AI-driven actions to established incident classifications, escalation paths, and crisis management protocols. This alignment preserves institutional knowledge while enhancing execution speed.
Equally critical is workforce integration. Analysts, engineers, legal teams, and executives must understand how AI recommendations are generated and how to intervene when judgment calls arise. Training, tabletop exercises, and simulation environments help organizations internalize AI-assisted workflows, transforming them into trusted operational assets rather than opaque tools.
Strategic and Long Term Benefits of Intelligent Incident Response
The long-term value of AI cybersecurity incident response extends beyond immediate threat mitigation. Over time, these systems accumulate institutional memory, learning from prior incidents to refine future responses. Patterns once invisible become predictable, allowing organizations to preempt entire classes of attacks through informed design changes.
This cumulative intelligence reshapes defensive posture. Security teams shift from alert fatigue to strategic analysis, while leadership gains confidence in the organization’s ability to absorb and adapt to disruption. Incident response becomes not merely a control function, but a driver of organizational learning and operational maturity.

Final Thought
AI-driven incident response marks a turning point in Cybersecurity’s evolution from reactive defense to adaptive resilience. Its true strength lies not in automation alone, but in the disciplined integration of machine intelligence with human accountability. When thoughtfully implemented, it fosters clarity under pressure, proportion under uncertainty, and continuity amid disruption.
As organizations increasingly depend on complex digital ecosystems, the ability to respond intelligently to failure becomes as important as preventing it. AI cybersecurity incident response offers a path toward that capability, one grounded in awareness, responsiveness, and an enduring commitment to operational integrity.

Subscribe to CyberLens
Cybersecurity isn’t just about firewalls and patches anymore — it’s about understanding the invisible attack surfaces hiding inside the tools we trust.
CyberLens brings you deep-dive analysis on cutting-edge cyber threats like model inversion, AI poisoning, and post-quantum vulnerabilities — written for professionals who can’t afford to be a step behind.
📩 Subscribe to The CyberLens Newsletter today and Stay Ahead of the Attacks you can’t yet see.